



The core of Feedly for Threat Intelligence is an AI engine, called Leo, that automatically gathers, analyzes, and prioritizes intelligence from millions of sources in real-time.
In this article, we’ll show you how to use Leo to:
Before we look at those four use cases, let’s start with a short overview of how Leo works.
Leo reads millions of articles, reports, and social media posts every day and automatically tags key threat intelligence concepts: critical vulnerabilities, malware families, threat actors, indicators of compromise, ATT&CK techniques, companies, vendors, industries, etc.
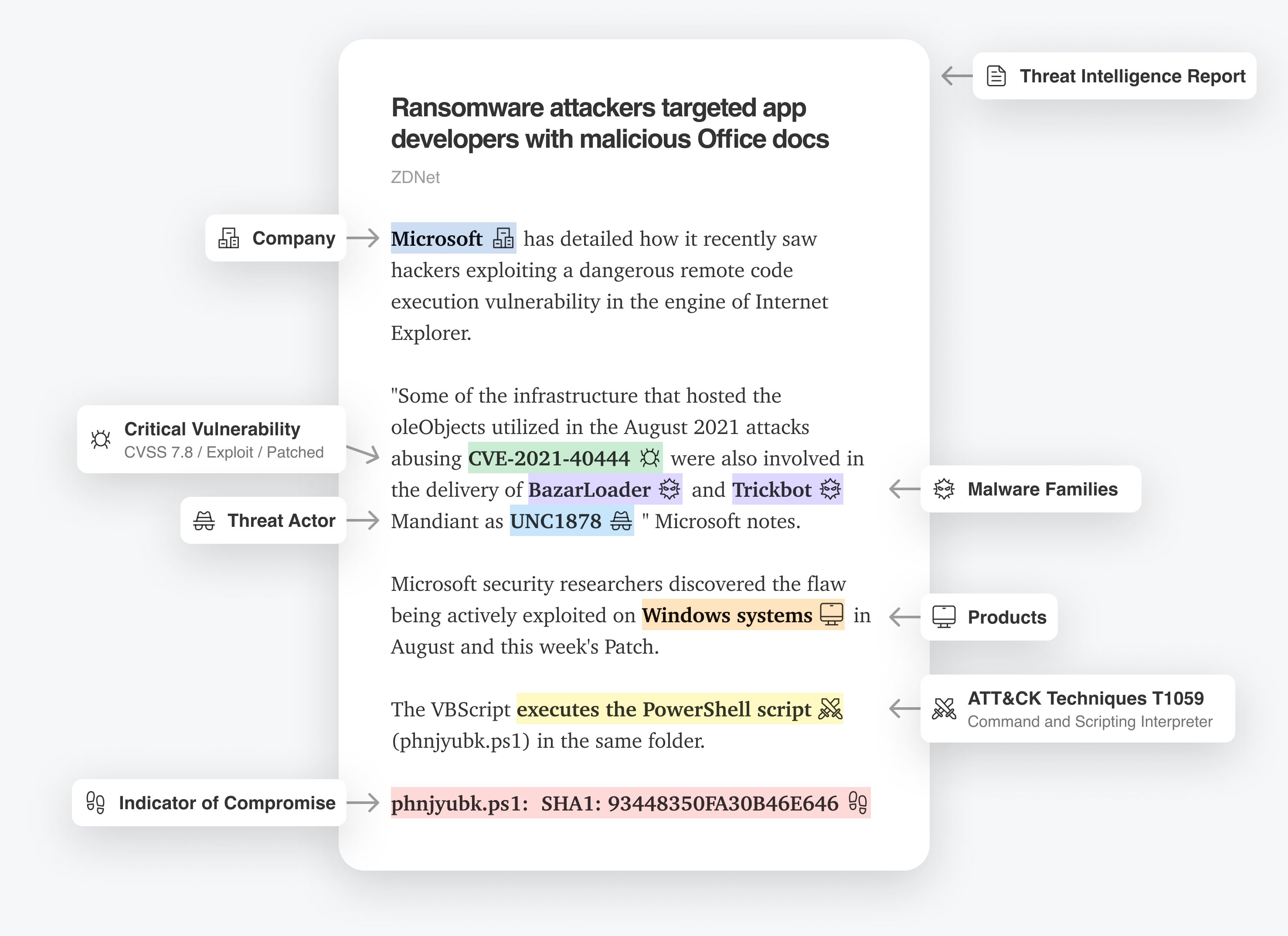
All this information is at your fingertips in near real-time via a powerful and intuitive search and tracking interface called Leo Web Alerts.
Curious how it works? Let’s take a look at a Leo Web Alert designed to track critical vulnerabilities and zero-days related to Cisco Systems:
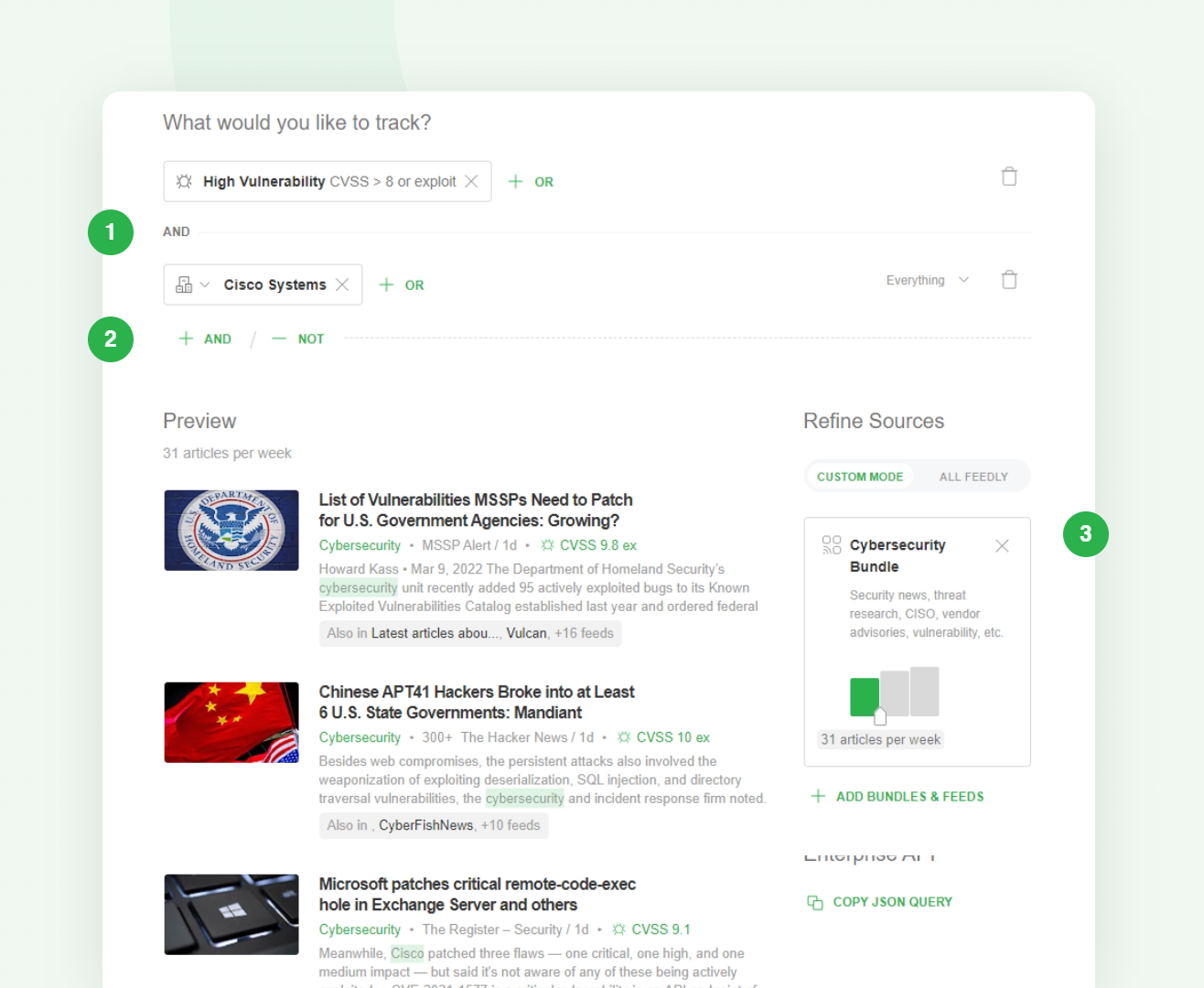
Creating a Leo Web Alert is a three-step process:
Leo Web Alerts are feeds you can add to a team or personal folder. New articles, reports, or social media posts matching the specified Leo Concepts will appear in the Leo Web Alert feed.
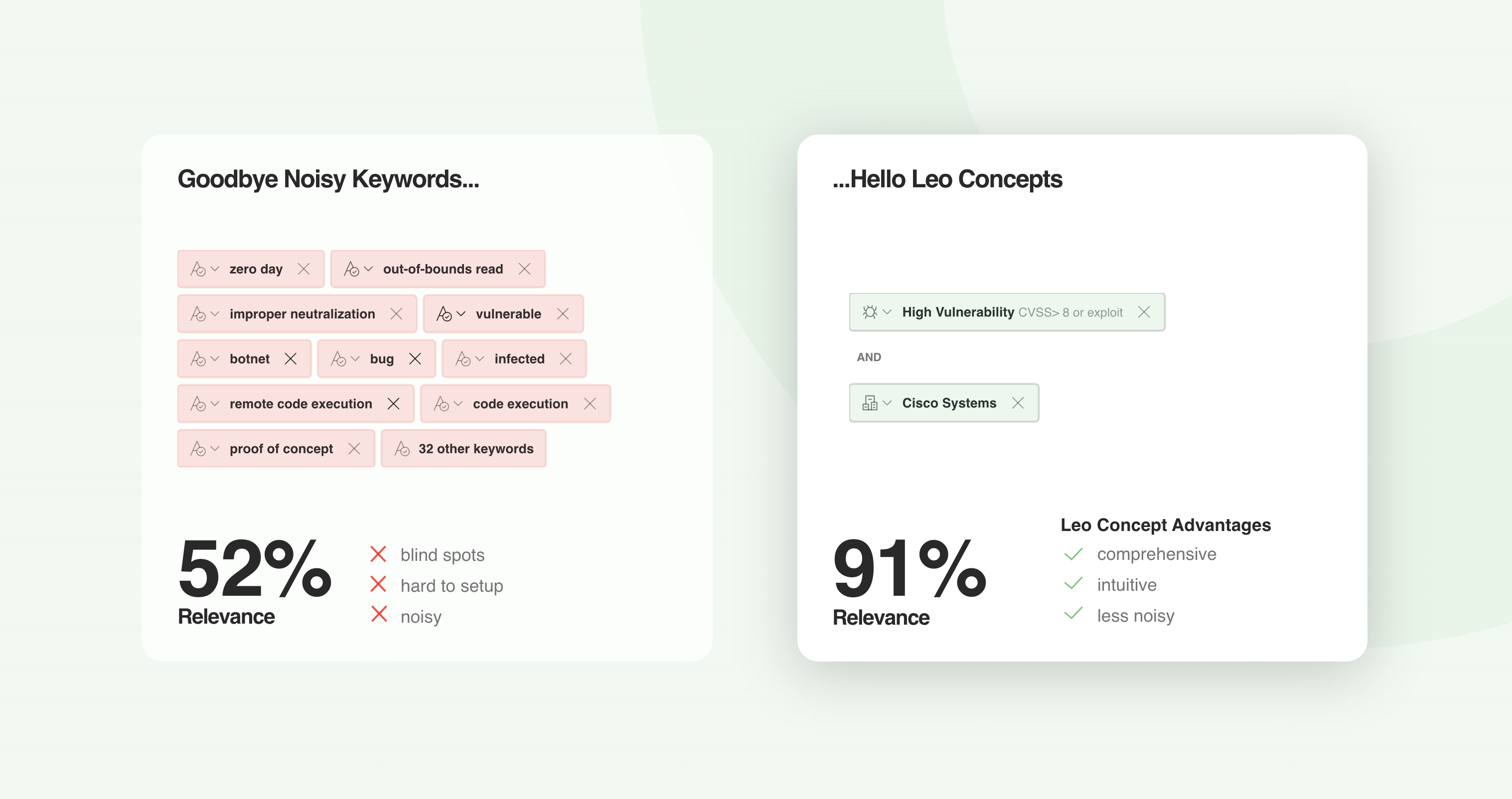
The power of Leo Web Alerts is that ‘High Vulnerability’ and ‘Cisco Systems’ are not simple keyword matches. These Leo Concepts are machine learning models that encapsulate a broader understanding of each concept:
Without Leo Concepts, gathering intelligence would require a tedious effort of trying to find a long list of the right keywords, leaving room for blind spots and lots of irrelevant results.
Feedly for Threat Intelligence comes with a wide range of pre-trained Leo Concepts so that you can easily translate your intelligence needs into Leo Web Alerts.
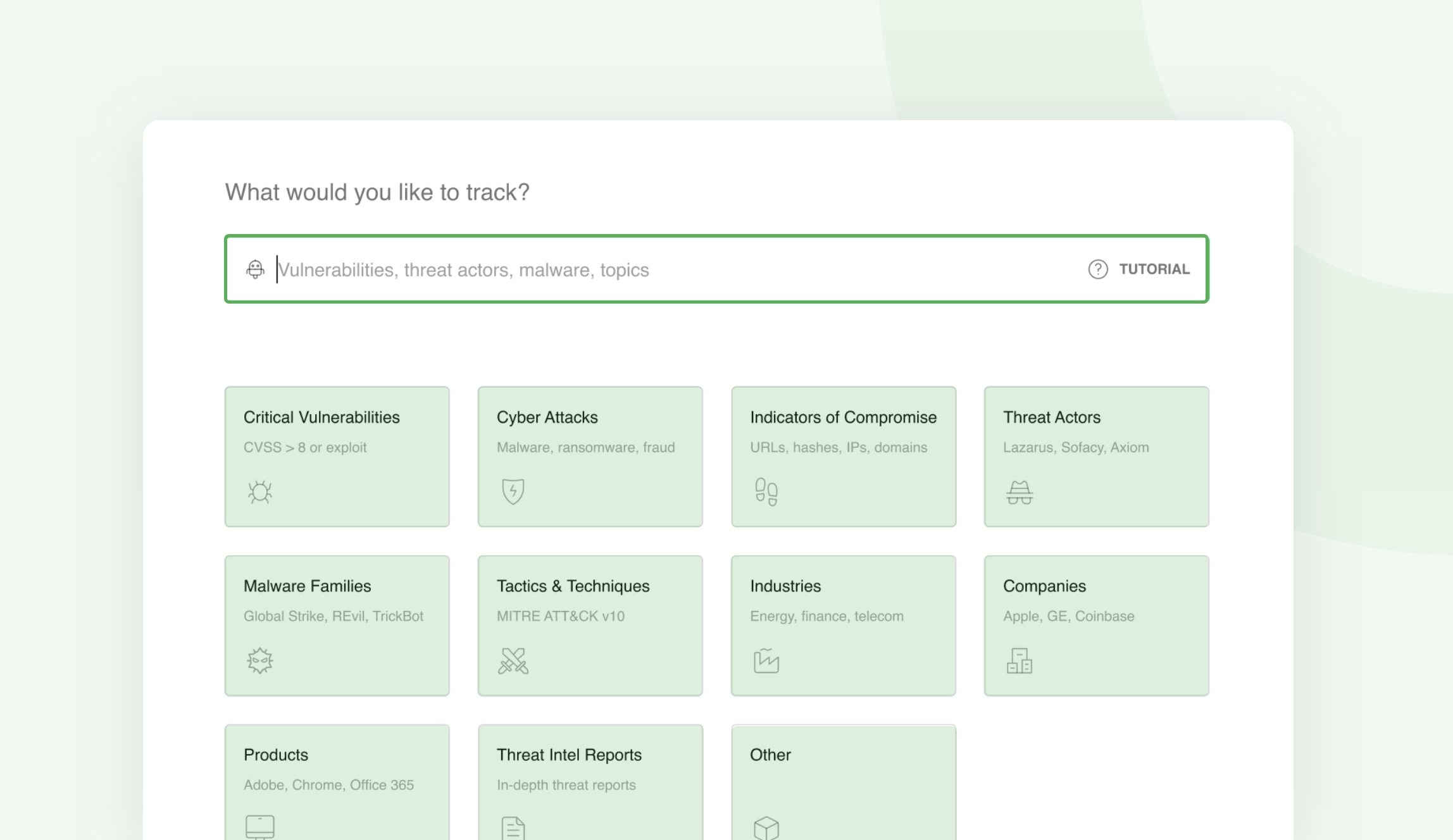
Let’s see how we can combine these Leo Concepts to proactively track specific threats and stay one step ahead of your adversaries.
Tracking the behavior of threat actors and malware families can be tedious and overwhelming, taking up valuable time that could be spent hunting for malicious activity in your environment.
That’s why Feedly has created a set of Leo Concepts that automatically tag threat actors, malware families, TTPs, and IoCs.
Let’s take a look at a Leo Web Alert designed to track the latest IoCs and TTPs related to Lazarus Group across threat intelligence reports published on the web:
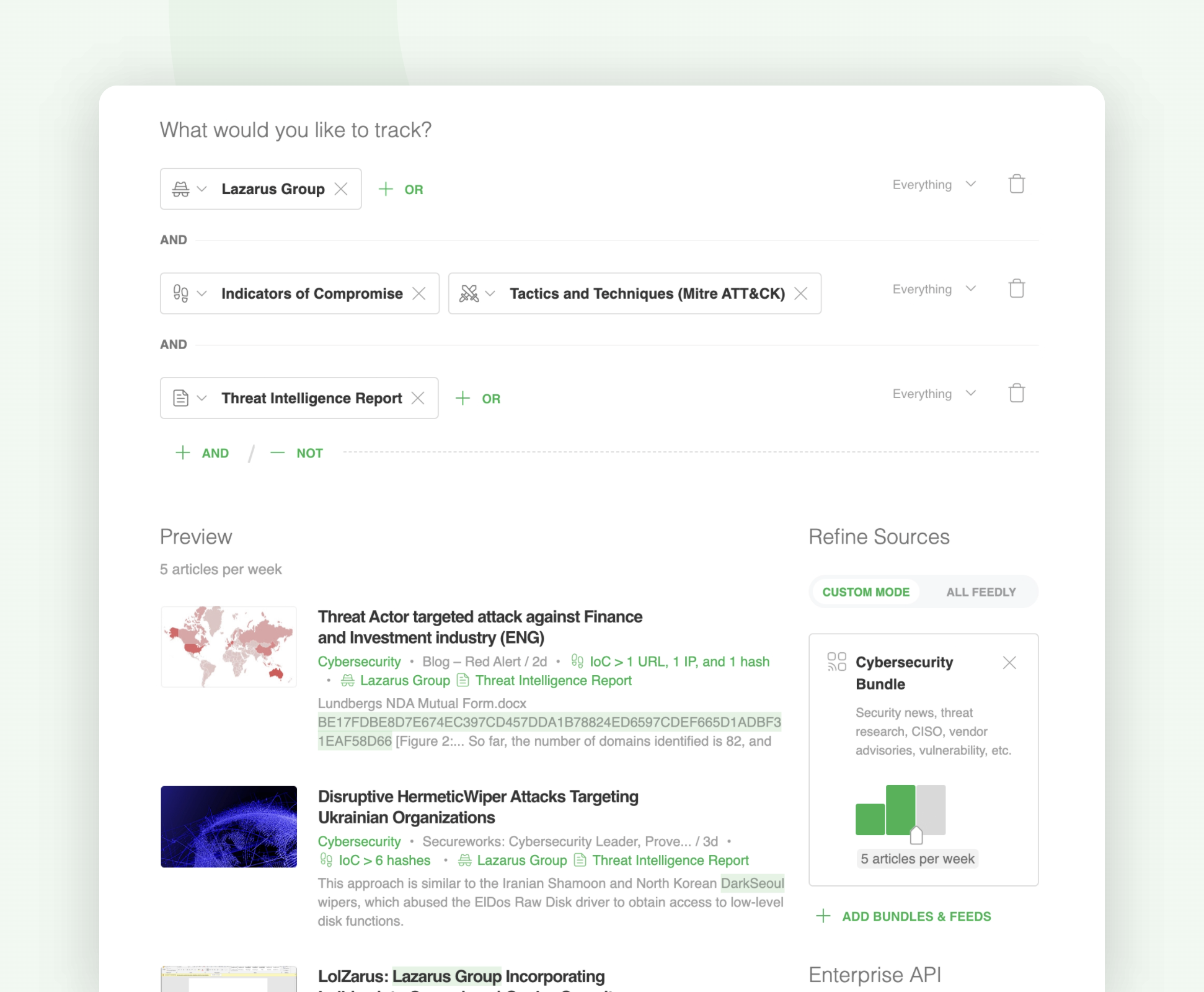
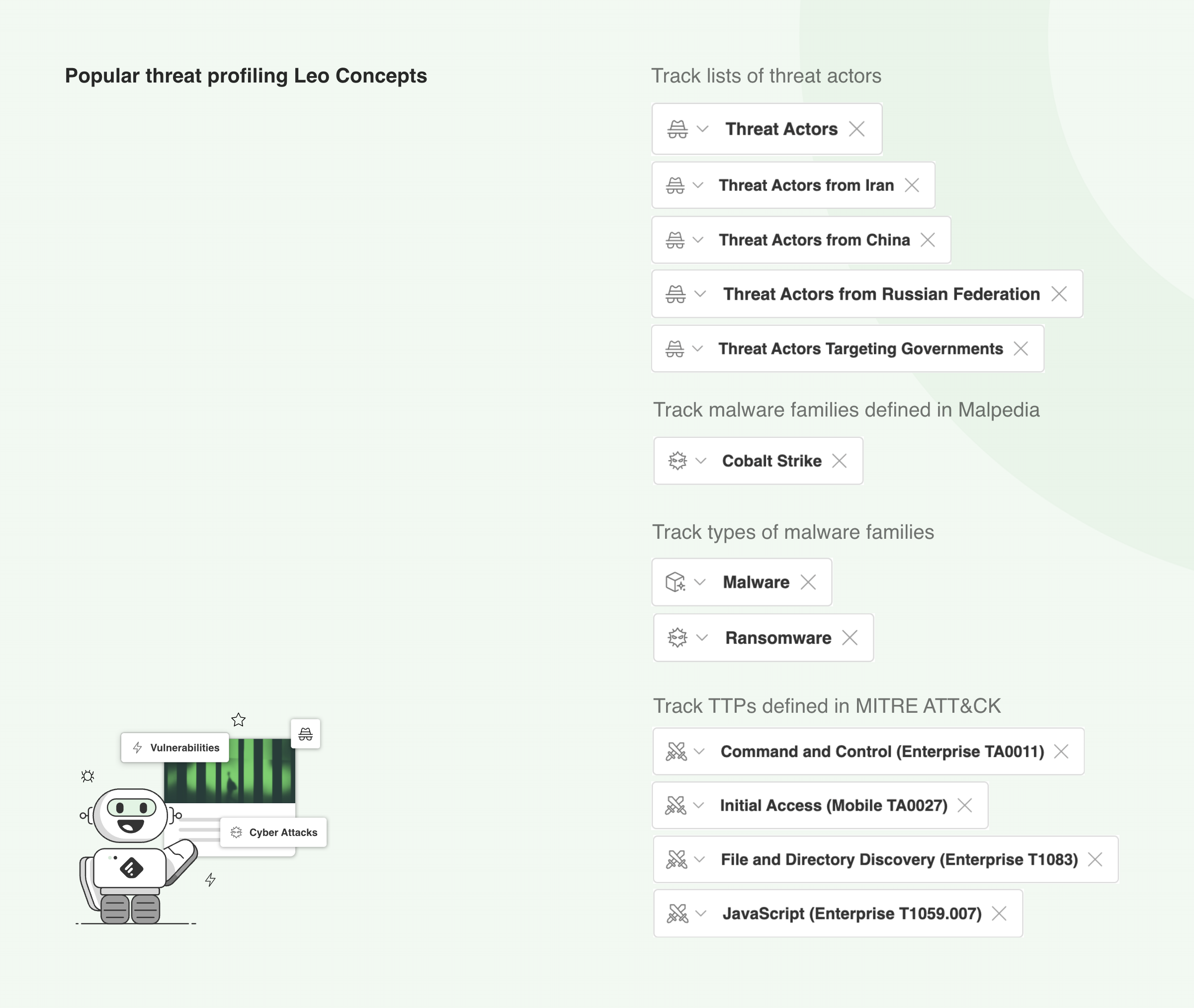
Here are some additional Leo Concepts you can use to broaden or narrow your threat profiling:
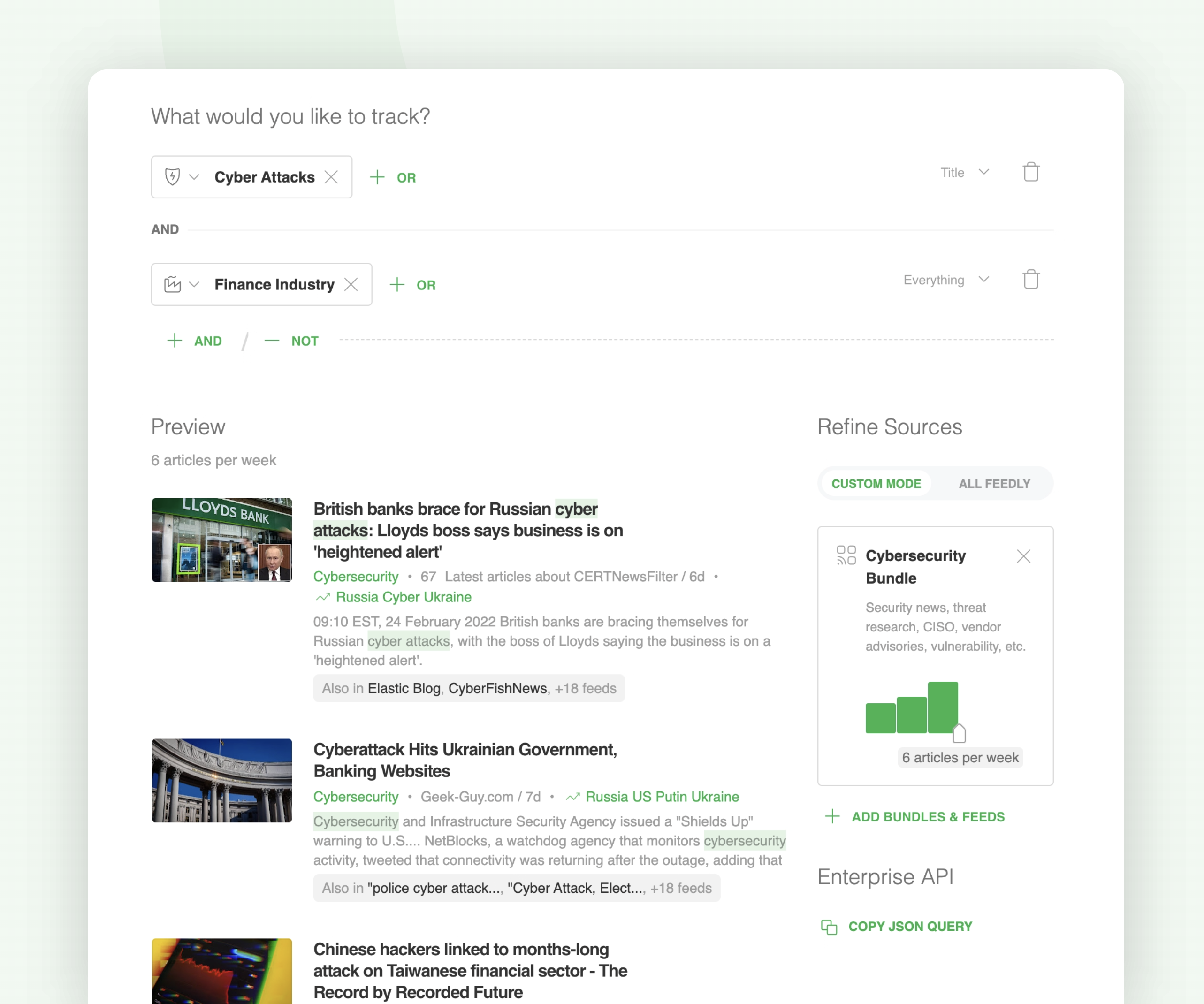
Staying up to date with the latest attacks against your industry can help you be better prepared when putting defenses in place, as well as help you learn about which threat actors to look out for so you can be more targeted when gathering intelligence.
Let’s take a look at a Leo Web Alert designed to gather intelligence about cyber attacks in the finance industry:
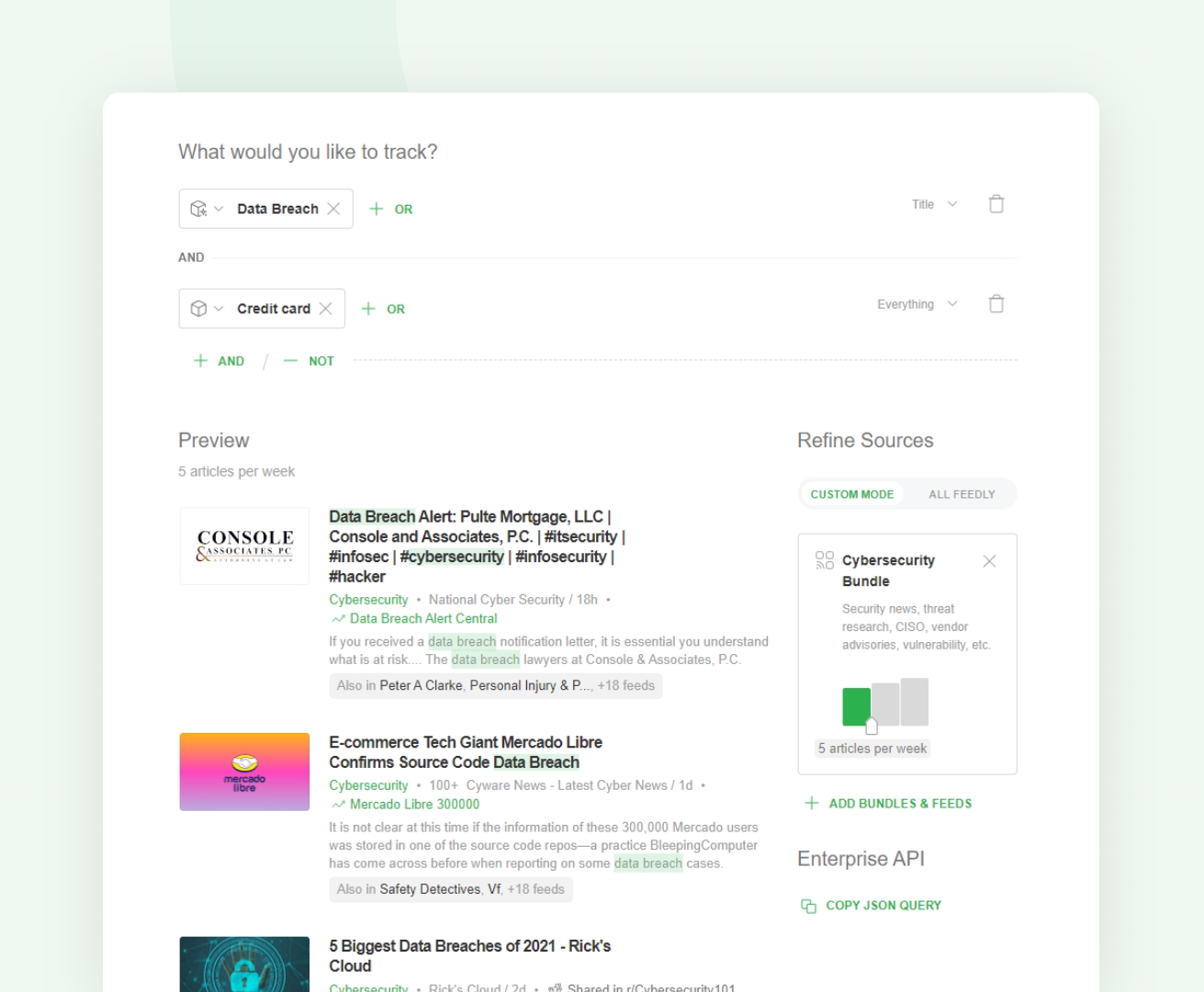
You can also easily narrow your focus on a specific type of attack:
Manually keeping ahead of new vulnerabilities and zero-days is an impossible task, but you can set up Leo Web Alerts to help you stay up to date on new vulnerabilities that come across the radar of the global cybersecurity community.
Feedly aggregates vulnerability information from NVD and over 20 vendor advisory sites — as well as monitoring many sources to find exploits for each CVE — in near real-time.
Let’s take a look at a Leo Web Alert designed to surface critical vulnerabilities and zero-days related to a vendor deployed in your environment:
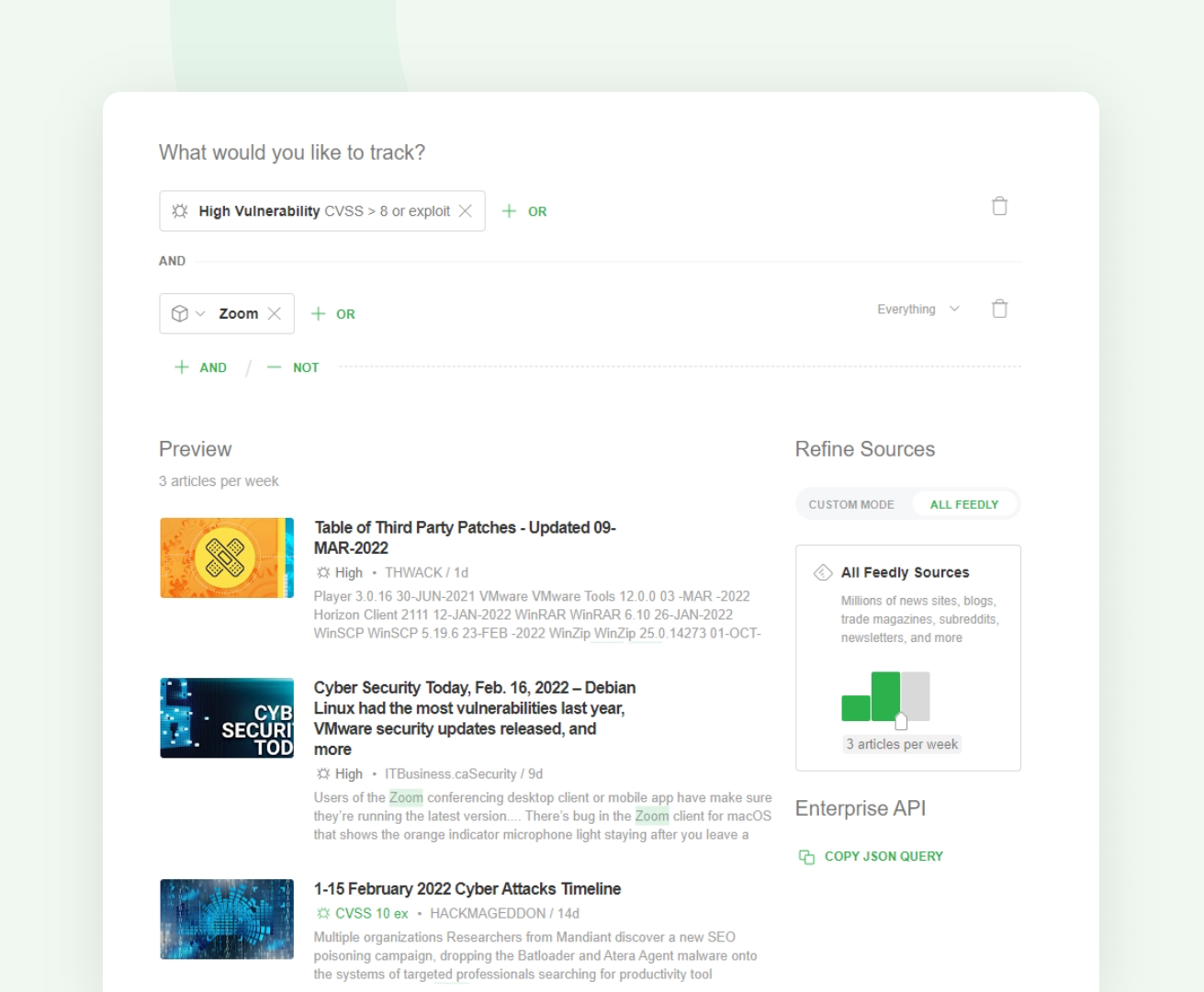
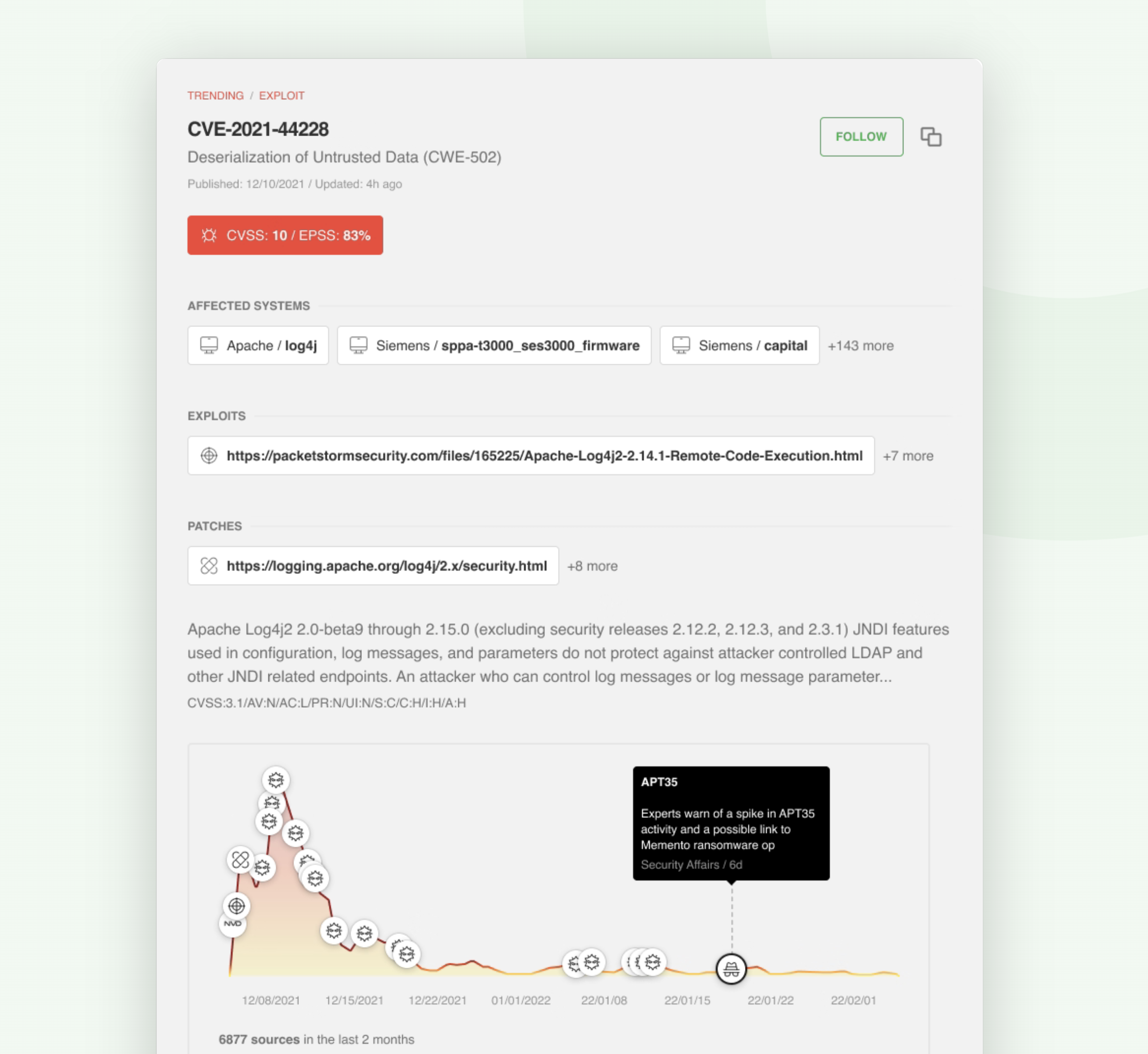
When you discover a new CVE, you can use the CVE intelligence card to get a 360 degree view of that vulnerability and decide if you should create a ticket for your response team.
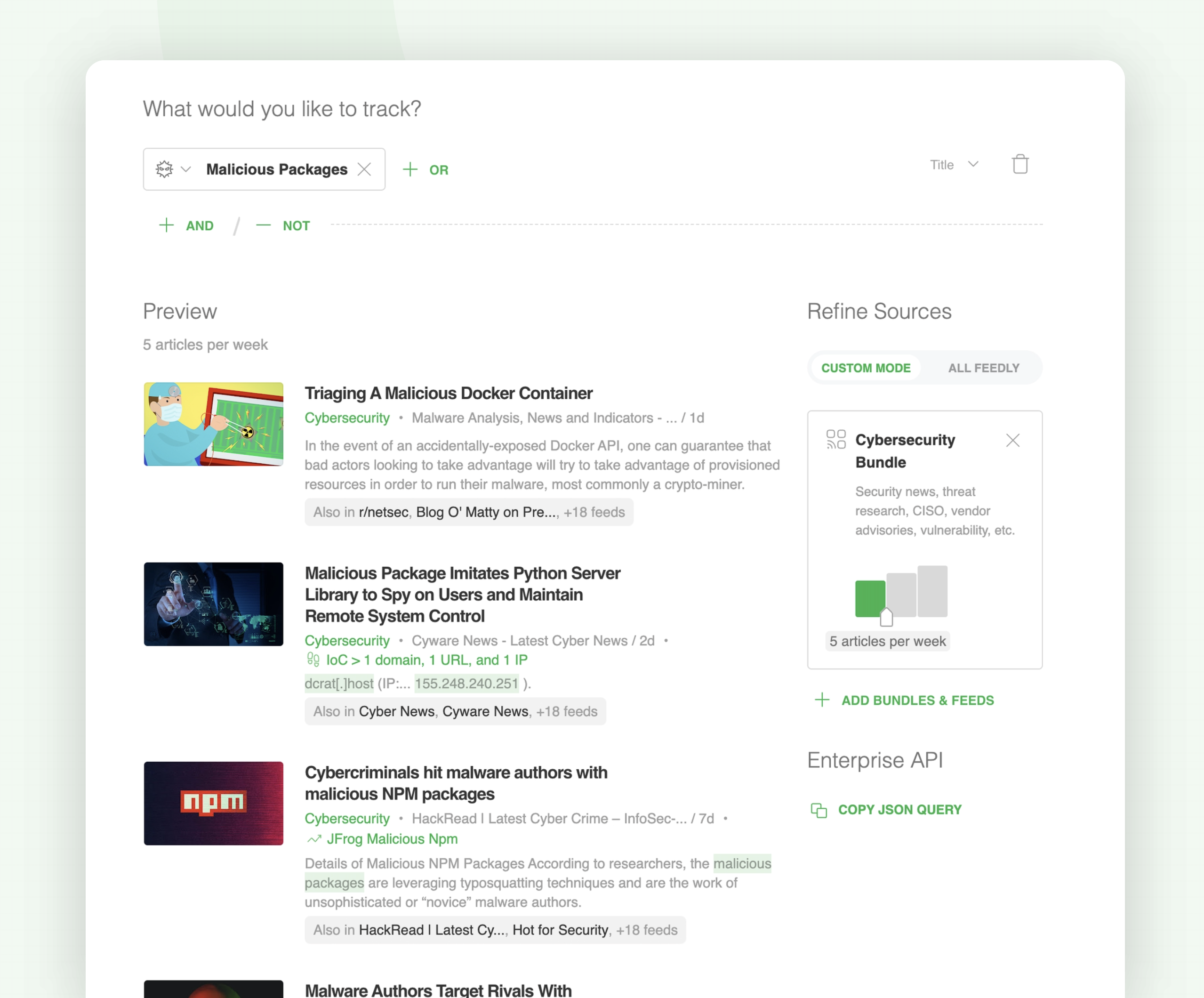
You can also use Leo Web Alerts to track niche cybersecurity topics.
Let’s take a look at a Leo Web Alert designed to gather intelligence about malicious, compromised, or hijacked packages:
Here are some additional Leo Concepts you can use to track niche cybersecurity topics:
The world’s leading cybersecurity teams use Feedly for their OSINT, so the product constantly improves based on their feedback.
Here is a roadmap of some of the new Leo Concepts we are researching:
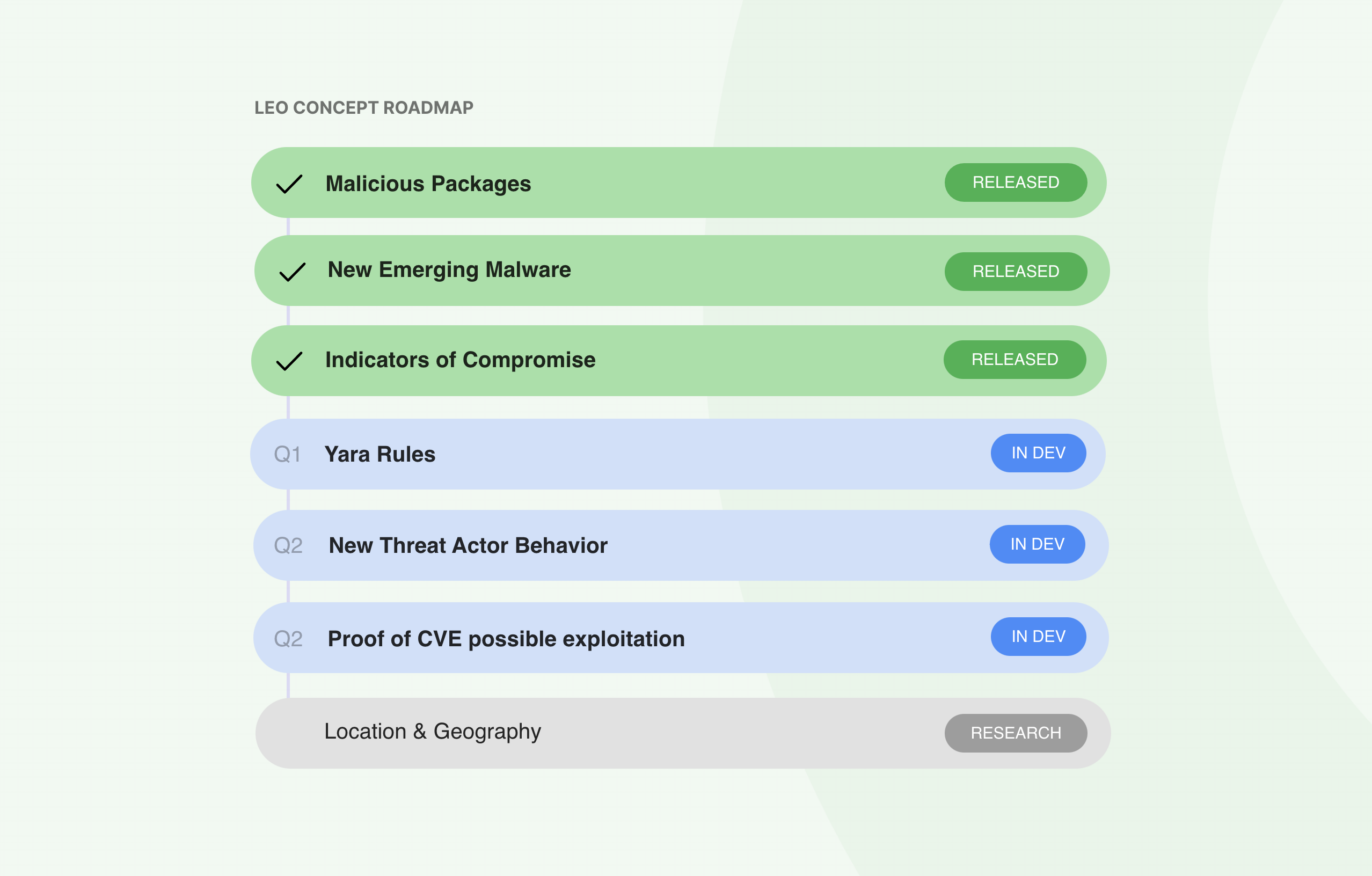
Feedly for Threat Intelligence customers can reach out to us at enterprise@feedly.com to give feedback on improving existing Leo Concepts or creating new ones to ensure that Feedly is working at full capacity to serve your Threat Intelligence needs.
All of these features, plus many more, are available as a part of Feedly for Threat Intelligence. To learn more about any of these features, or start a free 30-day trial, click the link below.
